Prefer not to host it yourself? Our NetLock RMM Cloud offers a secure and hassle-free solution starting at just €30 per month. Check it out here: NetLock RMM Cloud. Additionally, we provide on-premises installation services for those who prefer that option.
The server and web console can be installed either in the cloud or in offline environments, depending on your specific requirements.
¶ Roles
The NetLock server comes in six different roles:
- Comm
- Handles communication with the NetLock comm agent, including device information, policy, and events synchronization.
- Update
- Provides update packages for the agents, including the comm agent, health agent, remote agent, agent installer, and agent uninstaller.
- Trust
- Provides the hashes of all update packages. Agents contact the trust server to verify the hashes of downloaded packages.
- Remote
- Handles real-time connections between agents and the web console, such as the remote shell and file browser.
- Notification
- Sends third-party notifications, such as email, Microsoft Teams, Telegram, and ntfy.sh.
- File
- Provides a file storage service for downloading and uploading files. This can be used to download tools or files on the customer side.
¶ Basic Server Concept
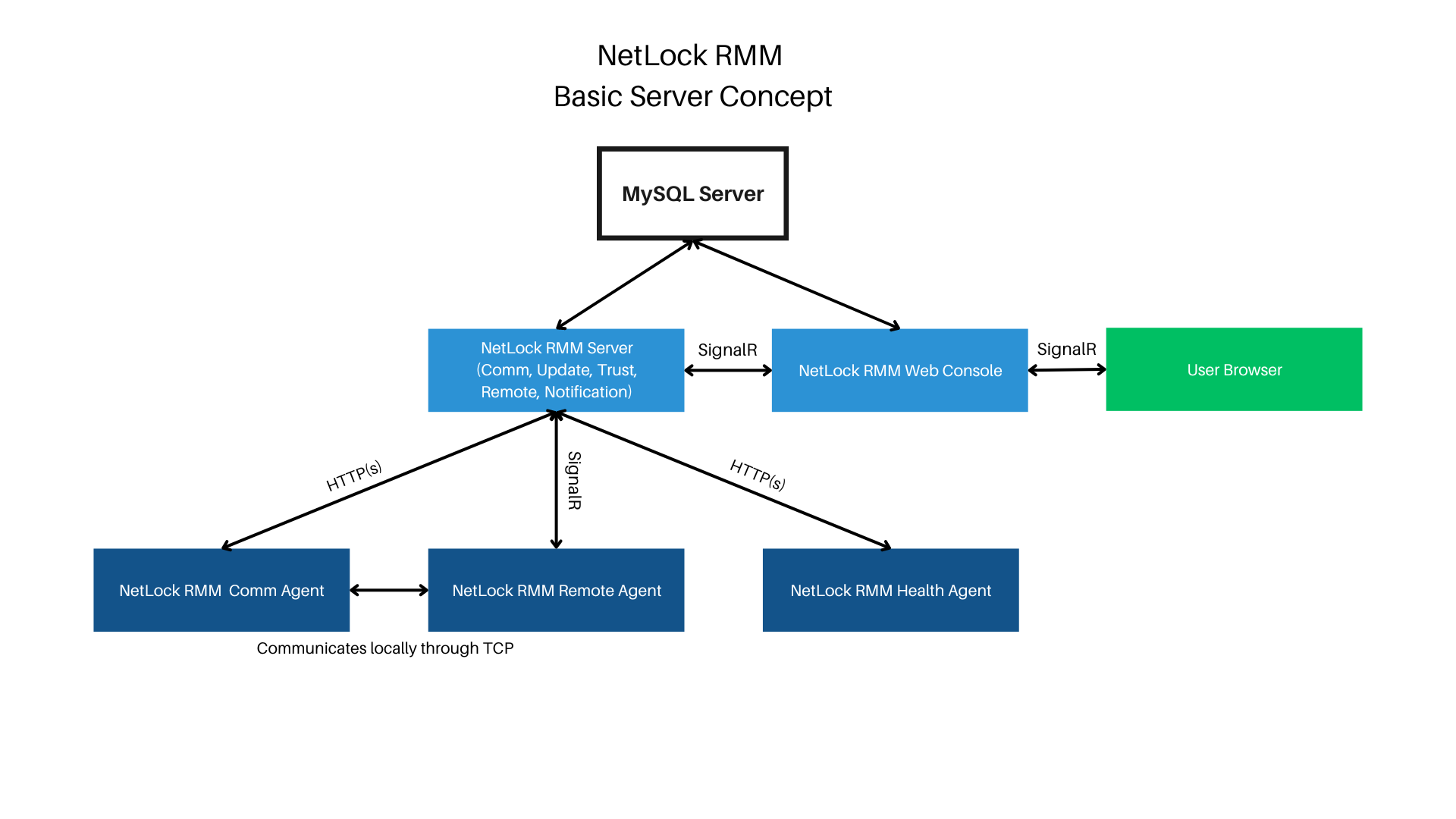
The agents only perform outgoing connections, so port forwarding is not required on these machines. The web console renders the content server-sided and then sends it to the user’s browser. Therefore, a permanent connection between the web console and user is necessary for operation. The web console communicates either directly with the SQL server or contacts the NetLock remote server through SignalR in cases like using the remote shell and file browser. Ensure the connection between the web console and NetLock remote server is possible. The web console should only be accessible from trusted environments.
¶ Advanced Server Concept
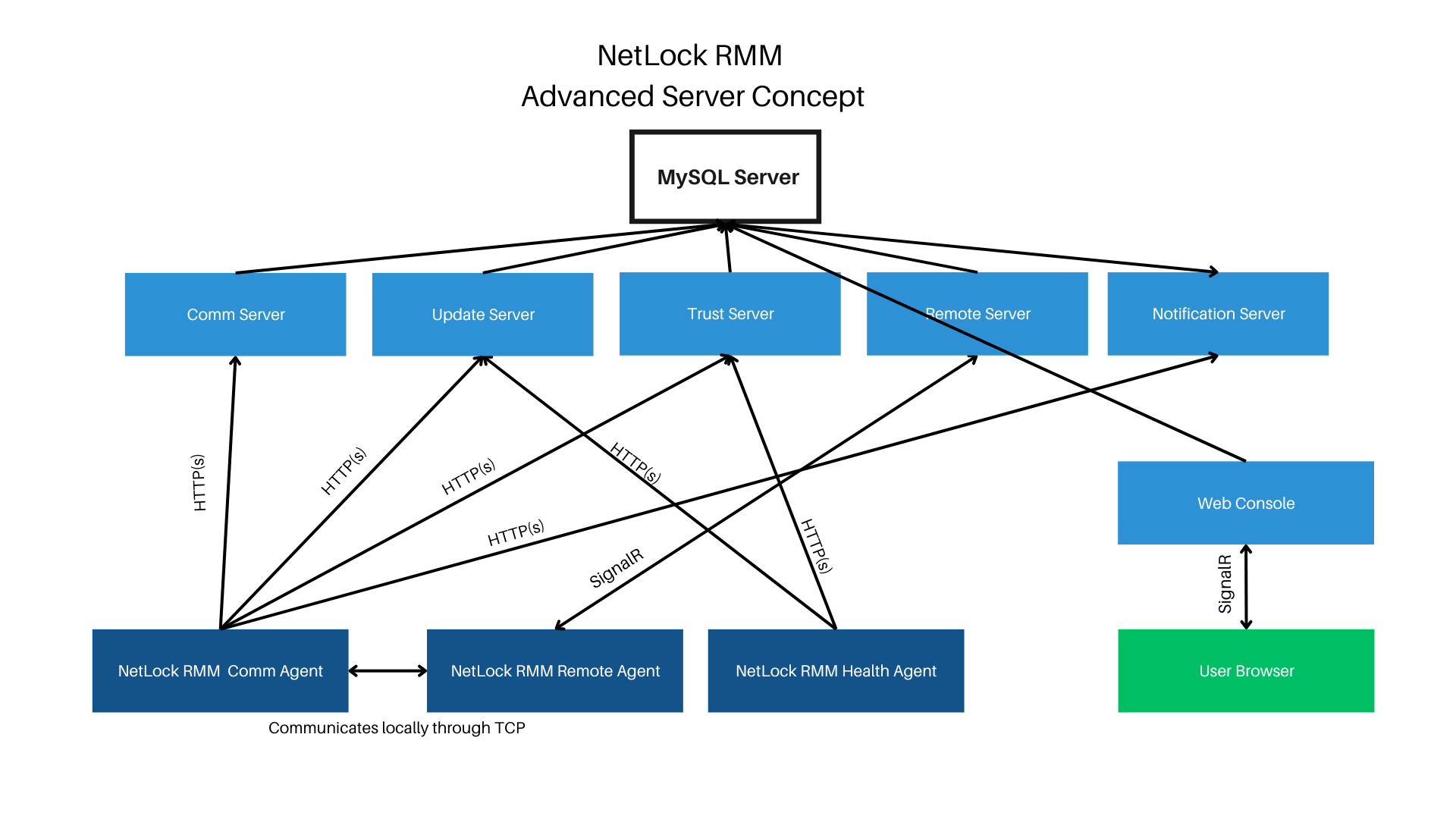
The agents only perform outgoing connections, so port forwarding is not required on these machines. The web console renders the content server-sided and then sends it to the user’s browser. Therefore, a permanent connection between the web console and user is necessary for operation. The web console communicates either directly with the SQL server or contacts the NetLock remote server through SignalR in cases like using the remote shell and file browser is being used. Ensure the connection between the web console and NetLock remote server is possible. The web console should only be accessible from trusted environments.
¶ What are the benefits of the advanced server concept?
- Performance
- Security
¶ Performance
In addition to using load balancers in your network, splitting the NetLock server into different roles can improve response times.
¶ Security
By dividing the server into different roles, you can significantly enhance security, especially against supply chain attacks like those seen with SolarWinds or Kaseya.
¶ Example Scenario
A classic update server supply chain attack works by supplying malicious update packages through a compromised update server to installed agents.
The NetLock comm agent contacts the NetLock comm server to verify if it is up-to-date. If the server indicates that it is outdated, the agent contacts the NetLock update server and downloads the NetLock agent installer. Before executing it, the NetLock comm agent contacts the NetLock trust server to request the hash of the downloaded package. If the local package hash differs from the hash provided by the NetLock trust server, the agent will not execute the downloaded installer.
In summary, if an attacker compromises your NetLock update server, they would still need to compromise the NetLock trust server to deploy a malicious update. Otherwise, the NetLock comm agent would not execute the downloaded package.
To continue, please follow the installation guides.