Prefer not to host it yourself? Our NetLock RMM Cloud offers a secure and hassle-free solution starting at just €60 per month and with no device limitation. Check it out here: NetLock RMM Cloud. Additionally, we provide on-premises installation services for those who prefer that option.
In this guide, we will cover the basic server installation.
The server and web console can be installed either in the cloud or in offline environments, depending on your specific requirements.
The network structure will be as follows:
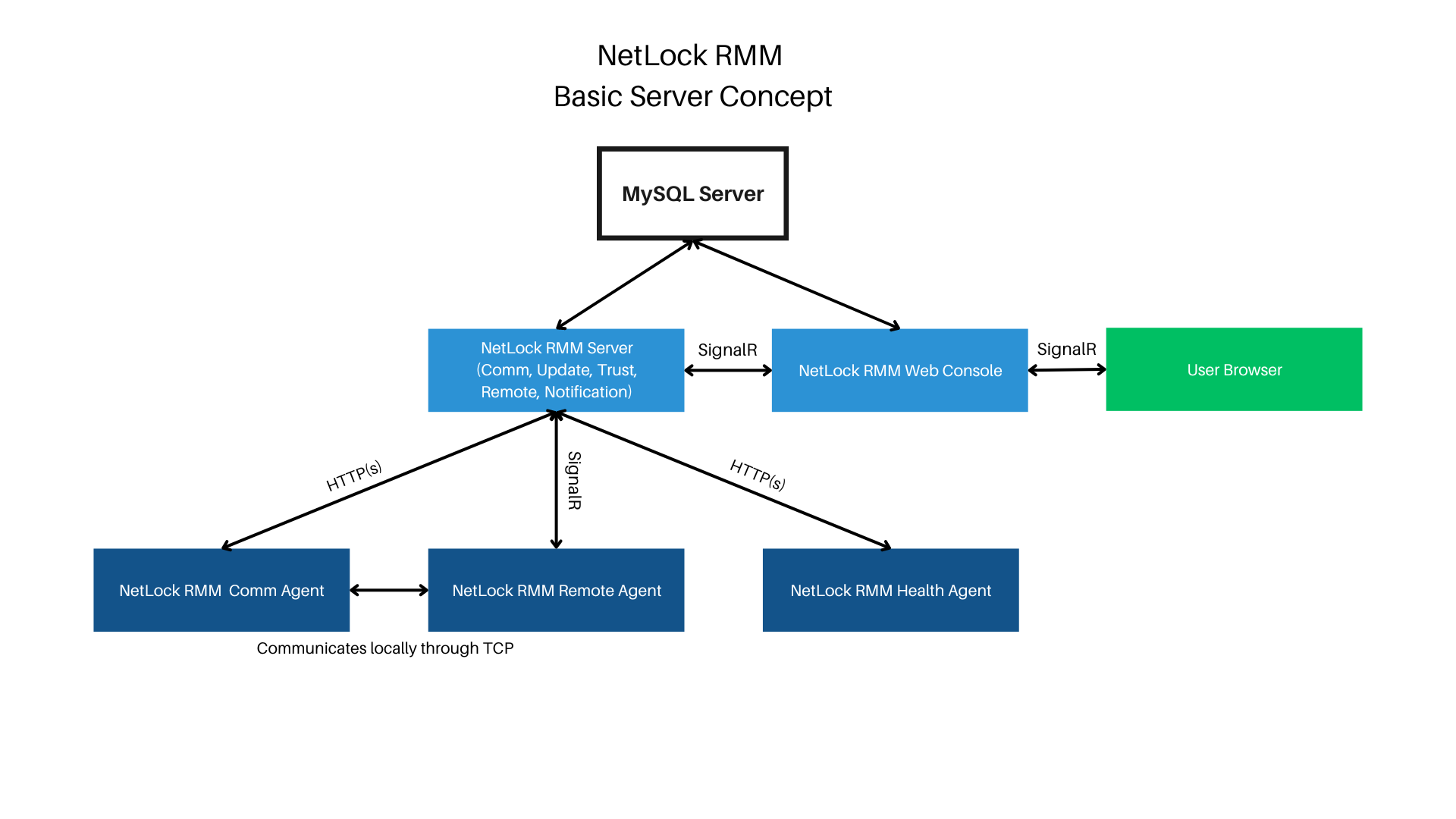
The agents only perform outgoing connections, so port forwarding is not required on these machines. The web console renders the content server-sided and then sends it to the admin user’s browser. Therefore, a permanent connection between the web console and admin user is necessary for operation. The web console communicates either directly with the SQL server or contacts the NetLock remote server through SignalR in cases like using the remote shell and file browser for real time processes. Ensure the connection between the web console and NetLock remote server is possible. The web console should only be accessible from trusted environments.
¶ Guided/Automated Installation
NetLock RMM can be deployed in any environment with Docker support. This also includes setups like cloudflare tunnels or similar. Our script builder focuses on typical server installations. If you need assistance in the deployment of NetLock RMM in non-standard environments, consider reaching out to our support team for guidance.
Navigate to https://members.netlockrmm.com/install and follow the steps from our installation tool.
Happy monitoring! 🥳
¶ Manual Installation
¶ Requirements
- Latest version of Docker
- MySQL Server, minimum version 8.0
- 2 Cores (may vary depending on the number of agents you monitor)
- 8 GB RAM
- Note: For high-performance, memory-optimized updates. If insufficient RAM is available, the setup may fail or NetLock RMM may run more slowly due to reliance on swap space. The backend is highly efficient, and 8 GB of RAM is sufficient for at least 2,000+ devices.
¶ Docker Tags
The following tags are available:
- latest
¶ NetLock RMM Web Console
- Create a directory in your Linux environment to store the appsettings.json file.
For example:
mkdir -p /home/netlock/web_console
- Create a directory in your Linux environment to store the Let’s Encrypt, internal data & logs.
For example:
mkdir -p /home/netlock/web_console/letsencrypt
mkdir -p /home/netlock/web_console/logs
mkdir -p /home/netlock/web_console/internal
- Next, create the appsettings.json file:
nano /home/netlock/web_console/appsettings.json
- Now, fill in the content of appsettings.json with the necessary configuration settings, like database configuration, logging settings, SSL, or other required options. Here’s an example structure to guide you:
{
"Logging": {
"LogLevel": {
"Default": "Warning",
"Microsoft": "Error",
"Microsoft.Hosting.Lifetime": "Warning"
},
"Custom": {
"Enabled": false
}
},
"AllowedHosts": "*",
"Kestrel": {
"Endpoint": {
"Http": {
"Enabled": true,
"Port": 80
},
"Https": {
"Enabled": false,
"Port": 443,
"Force": false,
"Hsts": {
"Enabled": true
},
"Certificate": {
"Path": "/certificates/certificate.pfx",
"Password": ""
}
}
},
"IpWhitelist": [],
"KnownProxies": []
},
"NetLock_Remote_Server": {
"Server": "netlock-rmm-server",
"Port": 7080,
"UseSSL": false
},
"NetLock_File_Server": {
"Server": "netlock-rmm-server",
"Port": 7080,
"UseSSL": false
},
"MySQL": {
"Server": "mysql-container",
"Port": 3306,
"Database": "vwffyq",
"User": "root",
"Password": "frfsL9FGmQWGbZDM",
"SslMode": "None",
"AdditionalConnectionParameters": "AllowPublicKeyRetrieval=True;"
},
"Webinterface": {
"Title": "NetLock RMM On Premises",
"Language": "en-US",
"Membership_Reminder": false,
"PublicOverrideUrl": "https://nl-webconsole.penguin-monitoring.de"
},
"Members_Portal_Api": {
"Enabled": true,
"ApiKeyOverride": "YOUR-MEMBERS-PORTAL-API-KEY"
}
}
Next, the individual entries in the appsettings.json file need to be customized to suit your environment. Adjust the values according to your environment’s requirements.
¶ NetLock RMM Server appsettings.json Example
Follow the same procedure.
- Create a directory in your Linux environment to store the appsettings.json file.
For example:
mkdir -p /home/netlock/server
- Create a directory in your Linux environment to store the Let’s Encrypt data & logs.
For example:
mkdir -p /home/netlock/server/letsencrypt
mkdir -p /home/netlock/server/logs
- Next, create a persistent files directory to enable the backend’s file server functionality. This directory will store all files managed by the server and ensure data persists even if the container is restarted or recreated:
mkdir -p /home/netlock/server/files
mkdir -p /home/netlock/server/internal
- Next, create the appsettings.json file:
nano /home/netlock/server/appsettings.json
- Now, fill in the content of appsettings.json with the necessary configuration settings, like database configuration, logging settings, SSL, or other required options. Here’s an example structure to guide you:
{
"Logging": {
"LogLevel": {
"Default": "Warning",
"Microsoft": "Error",
"Microsoft.Hosting.Lifetime": "Warning",
"Microsoft.AspNetCore.SignalR": "Error",
"Microsoft.AspNetCore.Http.Connections": "Error"
},
"Custom": {
"Enabled": false
}
},
"AllowedHosts": "*",
"Kestrel": {
"Endpoint": {
"Http": {
"Enabled": true,
"Port": 7080
},
"Https": {
"Enabled": false,
"Port": 7443,
"Force": false,
"Hsts": {
"Enabled": true
},
"Certificate": {
"Path": "/certificates/certificate.pfx",
"Password": ""
}
}
},
"Roles": {
"Comm": true,
"Update": true,
"Trust": true,
"Remote": true,
"Notification": true,
"File": true,
"LLM": true
}
},
"MySQL": {
"Server": "mysql-container",
"Port": 3306,
"Database": "vwffyq",
"User": "root",
"Password": "frfsL9FGmQWGbZDM",
"SslMode": "None",
"AdditionalConnectionParameters": "AllowPublicKeyRetrieval=True;"
},
"Members_Portal_Api": {
"Enabled": true,
"ApiKeyOverride": "YOUR-MEMBERS-PORTAL-API-KEY"
},
"Environment": {
"Docker": true
}
}
Next, the individual entries in the appsettings.json file need to be customized to suit your environment. Adjust the values according to your environment’s requirements.
¶ Docker Compose Example with Traefik Reverse Proxy
services:
traefik:
image: traefik:latest
container_name: traefik
command:
- '--providers.docker=true'
- '--providers.docker.exposedbydefault=false'
- '--entrypoints.web.address=:80'
- '--entrypoints.websecure.address=:443'
- '--entrypoints.web.http.redirections.entryPoint.to=websecure'
- '--entrypoints.web.http.redirections.entryPoint.scheme=https'
- '--entrypoints.web.http.redirections.entryPoint.permanent=true'
- '--certificatesresolvers.myresolver.acme.httpchallenge=true'
- '--certificatesresolvers.myresolver.acme.httpchallenge.entrypoint=web'
- '--certificatesresolvers.myresolver.acme.email=support@netlockrmm.com'
- '--certificatesresolvers.myresolver.acme.storage=/certificates/acme.json'
ports:
- '80:80'
- '443:443'
volumes:
- '/var/run/docker.sock:/var/run/docker.sock:ro'
- '/home/netlock/certificates/traefik:/certificates'
networks:
- netlock-network
restart: always
mysql:
image: mysql:8.0
container_name: mysql-container
environment:
MYSQL_ROOT_PASSWORD: "frfsL9FGmQWGbZDM"
MYSQL_DATABASE: "vwffyq"
volumes:
- /home/netlock/mysql/data:/var/lib/mysql
- /etc/localtime:/etc/localtime:ro
networks:
- netlock-network
restart: always
command:
- --skip-log-bin
- --innodb_buffer_pool_size=1G
- --innodb_log_file_size=256M
- --innodb_flush_log_at_trx_commit=2
- --max_connections=200
netlock-rmm-web-console:
image: nicomak101/netlock-rmm-web-console:latest
container_name: netlock-rmm-web-console
environment:
- TZ=Europe/Berlin
volumes:
- '/home/netlock/web_console/appsettings.json:/app/appsettings.json'
- '/home/netlock/web_console/internal:/app/internal'
- '/home/netlock/web_console/logs:/var/0x101 Cyber Security/NetLock RMM/Web Console/'
- '/home/netlock/certificates:/app/certificates'
- /etc/localtime:/etc/localtime:ro
labels:
- 'traefik.enable=true'
- "traefik.http.routers.webconsole.rule=Host(\`nl-webconsole.penguin-monitoring.de\`)"
- 'traefik.http.routers.webconsole.entrypoints=websecure'
- 'traefik.http.routers.webconsole.tls.certresolver=myresolver'
- 'traefik.http.services.webconsole.loadbalancer.server.port=80'
- "traefik.http.routers.webconsole-http.rule=Host(\`nl-webconsole.penguin-monitoring.de\`)"
- 'traefik.http.routers.webconsole-http.entrypoints=web'
- 'traefik.http.routers.webconsole-http.middlewares=redirect-to-https'
- 'traefik.http.middlewares.redirect-to-https.redirectscheme.scheme=https'
networks:
- netlock-network
restart: always
depends_on:
- mysql
netlock-rmm-server:
image: nicomak101/netlock-rmm-server:latest
container_name: netlock-rmm-server
environment:
- TZ=Europe/Berlin
volumes:
- '/home/netlock/server/appsettings.json:/app/appsettings.json'
- '/home/netlock/server/internal:/app/internal'
- '/home/netlock/server/files:/app/www/private/files'
- '/home/netlock/server/logs:/var/0x101 Cyber Security/NetLock RMM/Server/'
- '/home/netlock/certificates:/app/certificates'
- /etc/localtime:/etc/localtime:ro
labels:
- 'traefik.enable=true'
- "traefik.http.routers.rmmserver.rule=Host(\`nl-backend.penguin-monitoring.de\`)"
- 'traefik.http.routers.rmmserver.entrypoints=websecure'
- 'traefik.http.routers.rmmserver.tls.certresolver=myresolver'
- 'traefik.http.services.rmmserver.loadbalancer.server.port=7080'
- "traefik.http.routers.rmmserver-http.rule=Host(\`nl-backend.penguin-monitoring.de\`)"
- 'traefik.http.routers.rmmserver-http.entrypoints=web'
- 'traefik.http.routers.rmmserver-http.middlewares=redirect-to-https'
networks:
- netlock-network
restart: always
depends_on:
- mysql
networks:
netlock-network:
driver: bridge
¶ Troubleshooting
To view container logs, use:
docker logs CONTAINERID